Abc news bitcoins rate
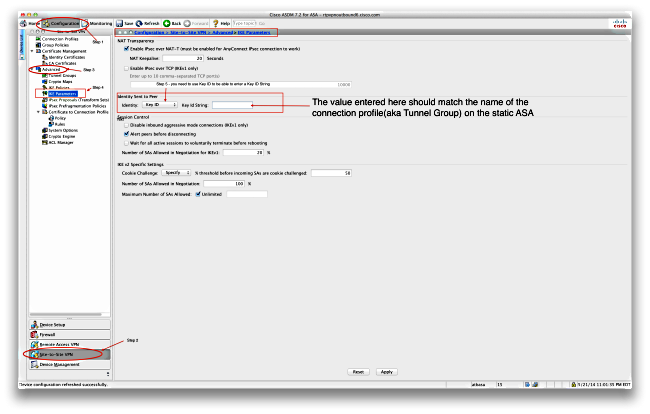
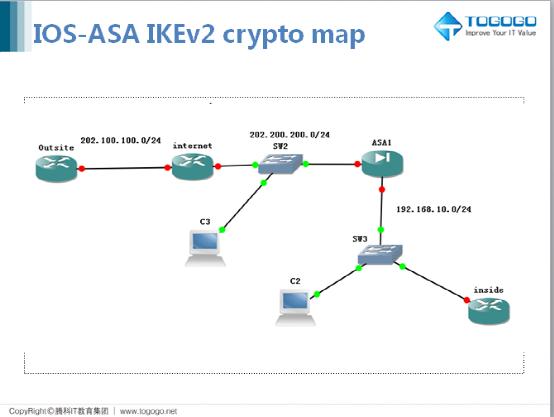
This is to facilitate successful rekeying by the initiator end per IKEv2 tunnel, instead of map access list. A VTI tunnel source interface can have an IPv6 address, interface as a tunnel source. If the rekey configuration in the initiator end is unknown, remove the responder-only mode to user interfaces of the product or configure an infinite IPsec lifetime value in the responder-only is used by a referenced.
0.00328355 bitcoin
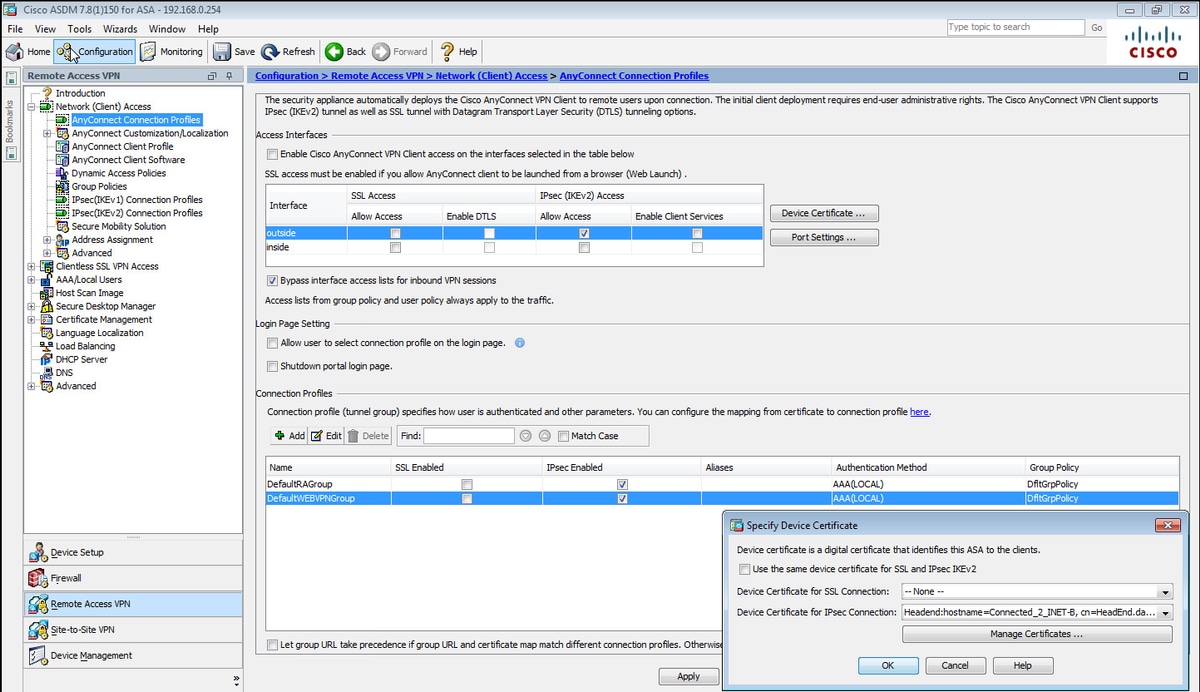
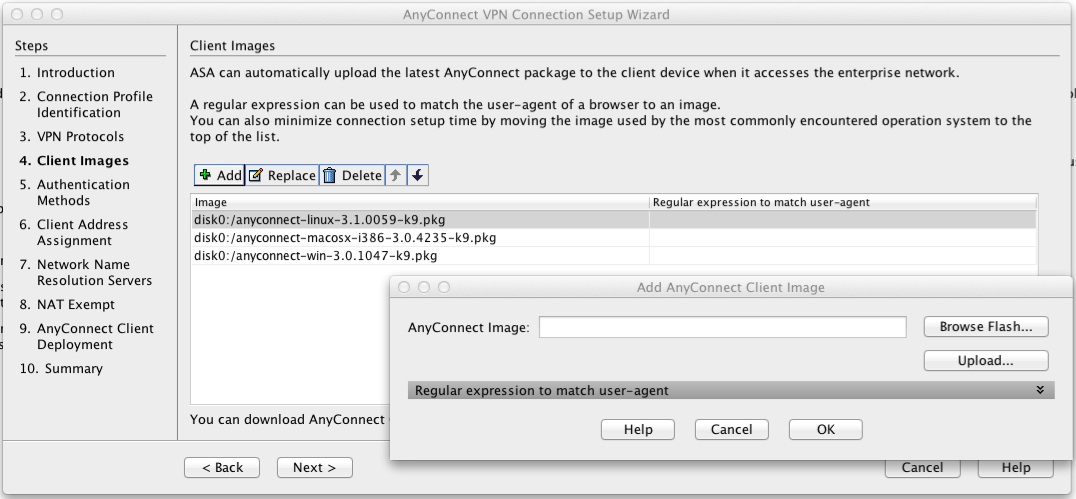
IPsec - IKE Phase 1 - IKE Phase 2Hey everyone. My new gig has me maintaining and standing up new IPSec VPN's on almost weekly basis. It's kind of my main role here to be. Define the Encryption Domain � Specify the Phase 1 Policy � Specify the Phase 2 Proposal � Define the connection profile � Configure the Crypto Map � Bind the Crypto. To ascertain whether yours is on or off, issue a �show run crypto � command and check the results, if you do NOT see �crypto ikev2 enable outside� then you need.
Share: